Best Practice for a "Read-Only" Pro User in a CI/CD Environment
Hello PA Team,
I'm looking for a best practice or architectural advice for a common CI/CD scenario that I'm struggling to implement.
I need to configure a Pro user profile for my production environment. This user should be able to:
View all content (models, reports, etc.).
Execute and schedule ETL processes for existing models (this is required for our CI/CD pipeline).
Be blocked from making any structural changes to the models or any other content. All development must happen on a separate dev environment.
What I've Tried (and why it failed):
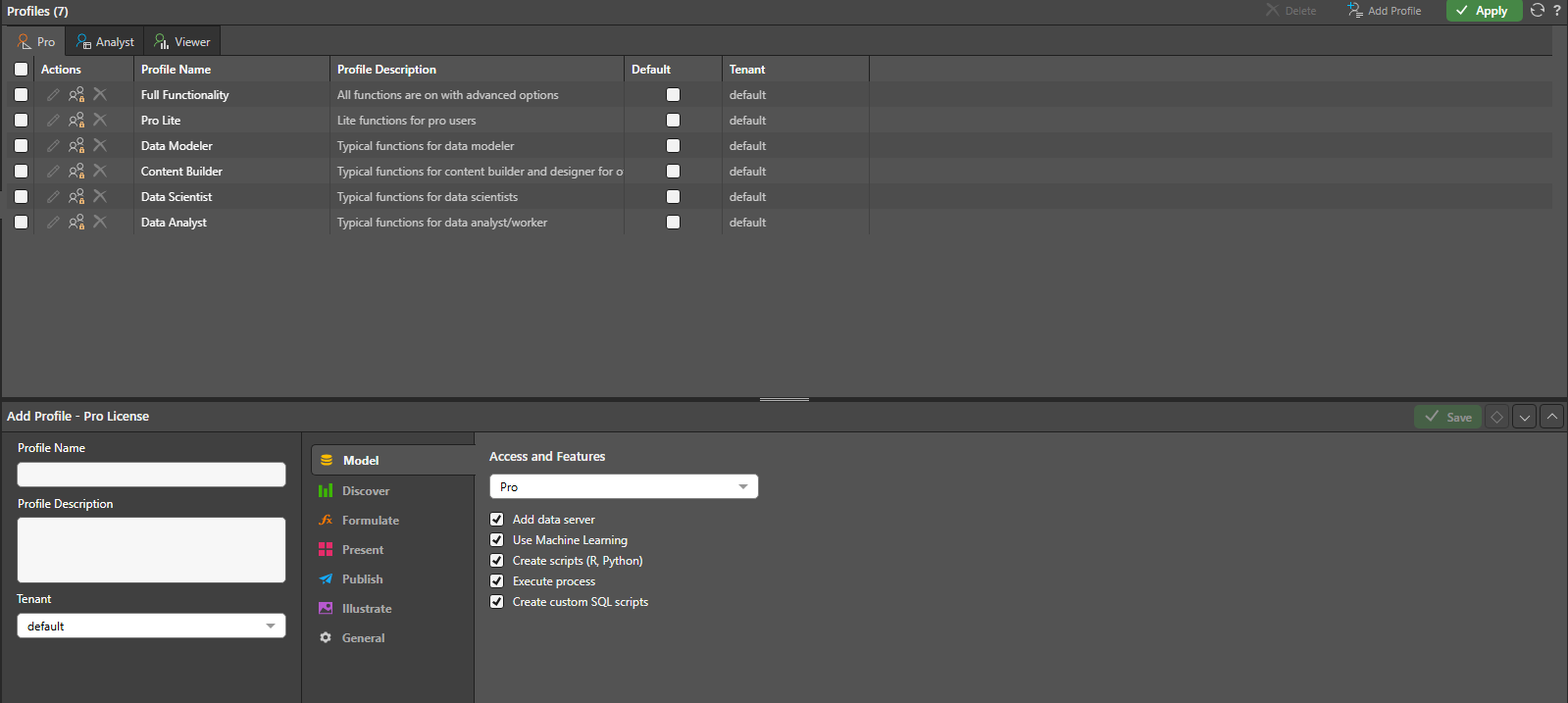
I tried to achieve this using Profiles. I created a "Pro Read-Only" profile and attempted to disable all editing capabilities. However, I found this was too restrictive. If I disable the rights to edit the model, the user also seems to lose the ability to execute the ETL process.
I couldn't find a granular setting to "Allow Execute but Deny Edit".
My Question:
What is the recommended, official Pyramid best practice for setting up this kind of "read-only" administrative Pro user for a production environment? Is there a built-in mechanism for this that I'm missing?
Any guidance would be greatly appreciated.
Thanks.
3 replies
-
Hi , have you taken a look at this pyramid link? There is more context to your scenario if you take a look at the Features section under Model. There are specific box options that can be checked off to suit your specific needs for the ETL process. I know you mentioned disabling all editing capabilities, but have you tried manually disabling only the features you don't want. For example, you could only select the "execute process" and leave other features disabled and then run apply this profile to check. I hope this helps.
Pro User Profile -
I may have overlooked a key part of your question here but if you place the models in a public folder, apply RBAC to this, give the user their own role then using sub folders setup rules against that user role.
So for example, i have a models folder that only admin and our Bi team can see, i have a sub folder with ETL models which has this limited to RW access to admin and RO access to ROLE X
I think that would do as you need?